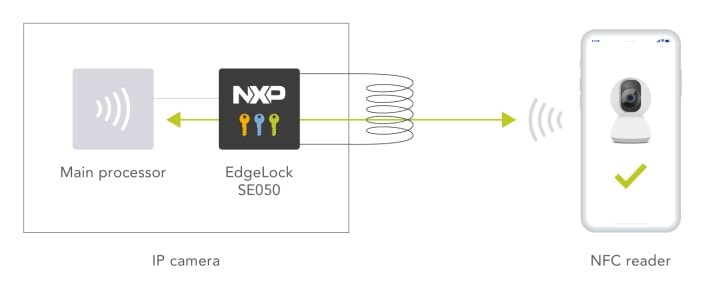
Protecting IP Cameras: From Serious Security Risk to Trusted Asset, with One IC | NXP Semiconductors
CVE-2021-28372: How a Vulnerability in Third-Party Technology Is Leaving Many IP Cameras and Surveillance Systems Vulnerable

Protecting IP Cameras: From Serious Security Risk to Trusted Asset, with One IC | NXP Semiconductors

The Hacker News on X: "Unauthenticated Remote Code Execution (RCE) vulnerability in Hikvision IP camera/NVR firmware (CVE-2021-36260) https://t.co/xbP0ViOkNi #infosec https://t.co/540njXHQZ7" / X

Nozomi probes deeper into security vulnerability that hackers can exploit to compromise Dahua IP cameras - Industrial Cyber
















